Anomaly Detection In Network Traffic Using Machine Learning
Machine learning identifies unusual network traffic, improving network path monitoring and security through real-time analysis.

Research topics
In today's digital landscape, efficient Packet Analysis is crucial for maintaining the integrity and security of network infrastructures. As the amount of Network Traffic continues to grow, traditional methods fall short, leading to a rise in the need for robust Anomaly Detection systems. Welcome to the world of Machine Learning, where we can take network security to the next level!
Understanding Network Path Monitoring
Network Path Monitoring plays an essential role in managing the flow of information within a network. It involves tracking the route that data takes as it travels from one point to another, providing visibility into network performance. By leveraging techniques from Data Science and Machine Learning, we can monitor traffic patterns in real-time to identify potential issues and deviations from normal behavior.
Access to real-time data enables organizations to respond promptly to emerging threats, enhancing their overall cybersecurity posture. Additionally, by continuously analyzing the network paths, businesses can ensure they've optimized their resources and improved overall operational efficiency.
The Role of Machine Learning in Anomaly Detection
Machine Learning enhances Anomaly Detection by providing automated approaches to identify irregular patterns that may signify potential intrusions or fault conditions. Traditional detection methods often rely on set rules and thresholds, which can fail to adapt to changing network conditions. On the other hand, utilizing machine learning techniques enables systems to learn from historical data, improving over time as they become more adept at identifying what constitutes normal network behavior.
For instance, algorithms can recognize patterns in Network Traffic, highlighting unusual spikes or drops, which may suggest undesirable activities or even cyber threats. This adaptability is vital in the ever-evolving landscape of Network Security.
Traffic Analysis for Enhanced Security
The process of Traffic Analysis complements anomaly detection perfectly. Analyzing network traffic not only aids in identifying suspicious activity but also facilitates the optimization of performance. With the help of Machine Learning algorithms, security teams can gain valuable insights into the types of traffic traversing their networks, enabling them to detect patterns that may otherwise go unnoticed.
As an added benefit, integrating advanced Intrusion Detection systems with machine learning capabilities allows for proactive threat mitigation, helping to safeguard sensitive data from malicious actors. This means that the more data we analyze, the better our defense mechanisms become.
Real-time Monitoring: A Game Changer for Cybersecurity
The need for Real-time Monitoring cannot be overstated. Businesses rely on constantly examining their network traffic to identify and respond to threats timely. By combining Machine Learning with real-time data collection, organizations can detect anomalies as they occur, drastically reducing the risk of a successful attack.
By investing in effective monitoring solutions, like those from Datadog, businesses can leverage advanced analytics to maintain real-time oversight of their network environments. This real-time responsiveness allows for swift action against potential security breaches, enhancing overall Network Security.
Performance Monitoring and Its Importance
However, it's essential to balance Performance Monitoring with Network Security. Monitoring tools must consider critical performance metrics, ensuring that the network remains efficient while simultaneously identifying threats. Poorly configured monitoring tools may create false positives, which could lead to unnecessary disruptions and drain valuable IT resources.
By utilizing sophisticated data techniques, organizations can uncover insights that inform not only security strategies but also performance optimizations. Understanding network pathways opens doors for improved experience and efficiency while maintaining stronger security postures.
Conclusion
In conclusion, the application of Machine Learning in Anomaly Detection offers substantial benefits for organizations looking to secure their networks in an increasingly complex cyber landscape. By investing in solutions that provide Packet Analysis, Traffic Analysis, and continuous Network Path Monitoring, companies can protect their assets and bolster their cybersecurity measures.
Those looking for a powerful monitoring solution for their networks may consider exploring options like SurePath for enhanced visibility and control. With continuous advancements in the fields of data science and machine learning, the possibilities for anomaly detection are endless!
Posts Relacionados
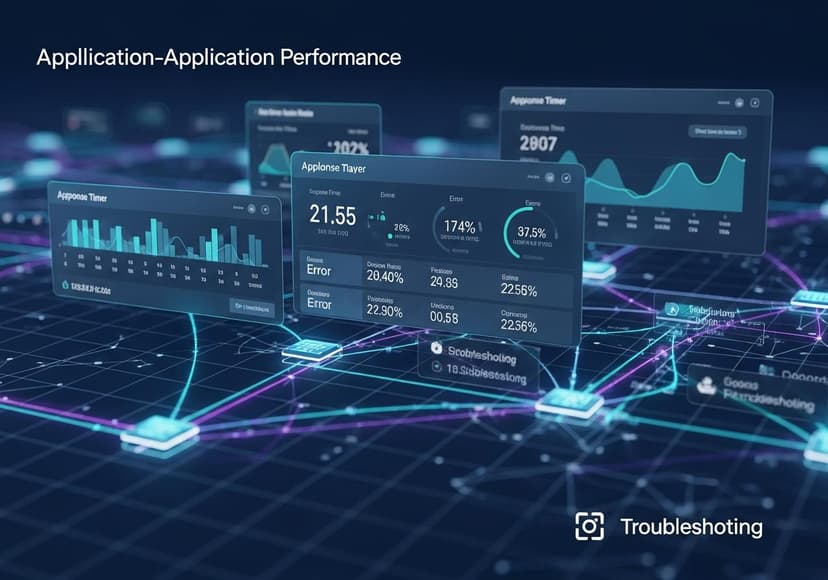
Application Performance Monitoring
Network diagnostics provide insights. Performance bottlenecks identified, resolved, enhancing network efficiency and user experience.
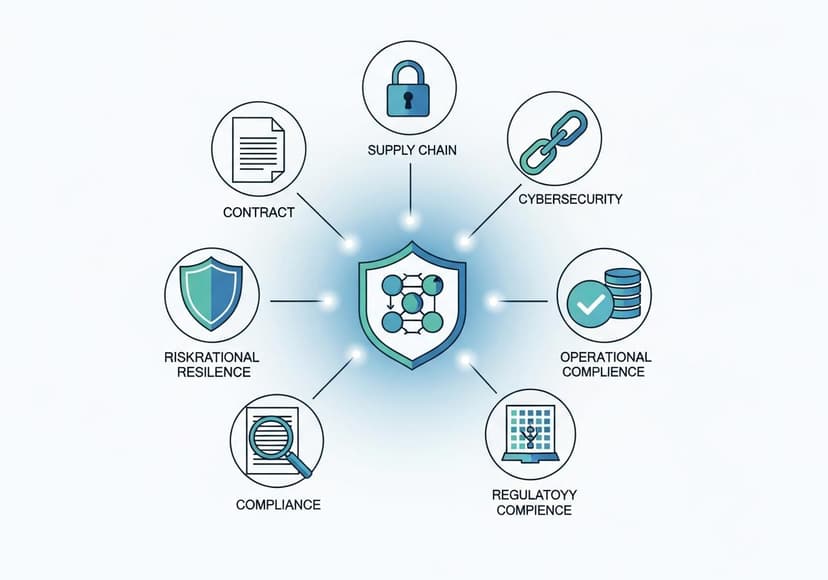
Assessing Thirdparty Risk
Effective management of third-party risk protects business operations through diligent evaluation and proactive mitigation strategies.
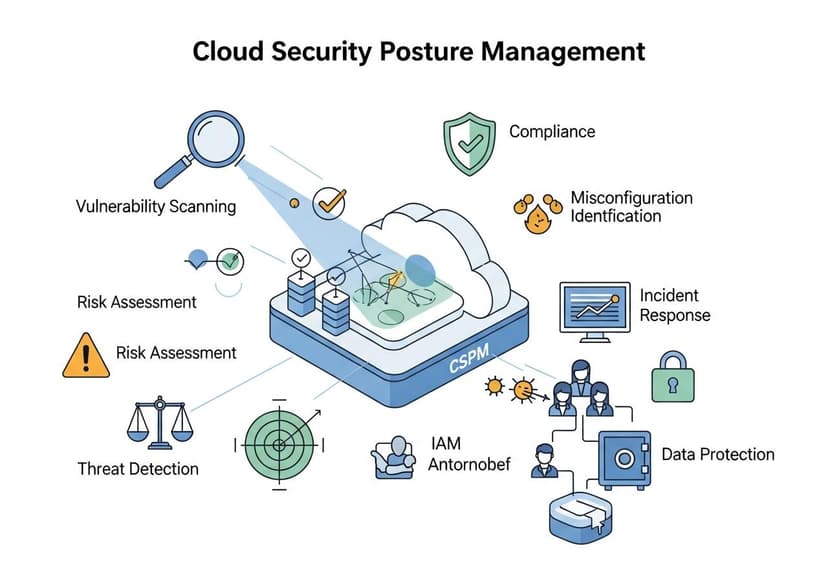
Cloud Security Posture Management Best Practices
Proactive cloud security relies on continuous monitoring, automated remediation, and consistent configuration for enhanced protection.