Cloud Security Posture Management Best Practices
Proactive cloud security relies on continuous monitoring, automated remediation, and consistent configuration for enhanced protection.
Research topics
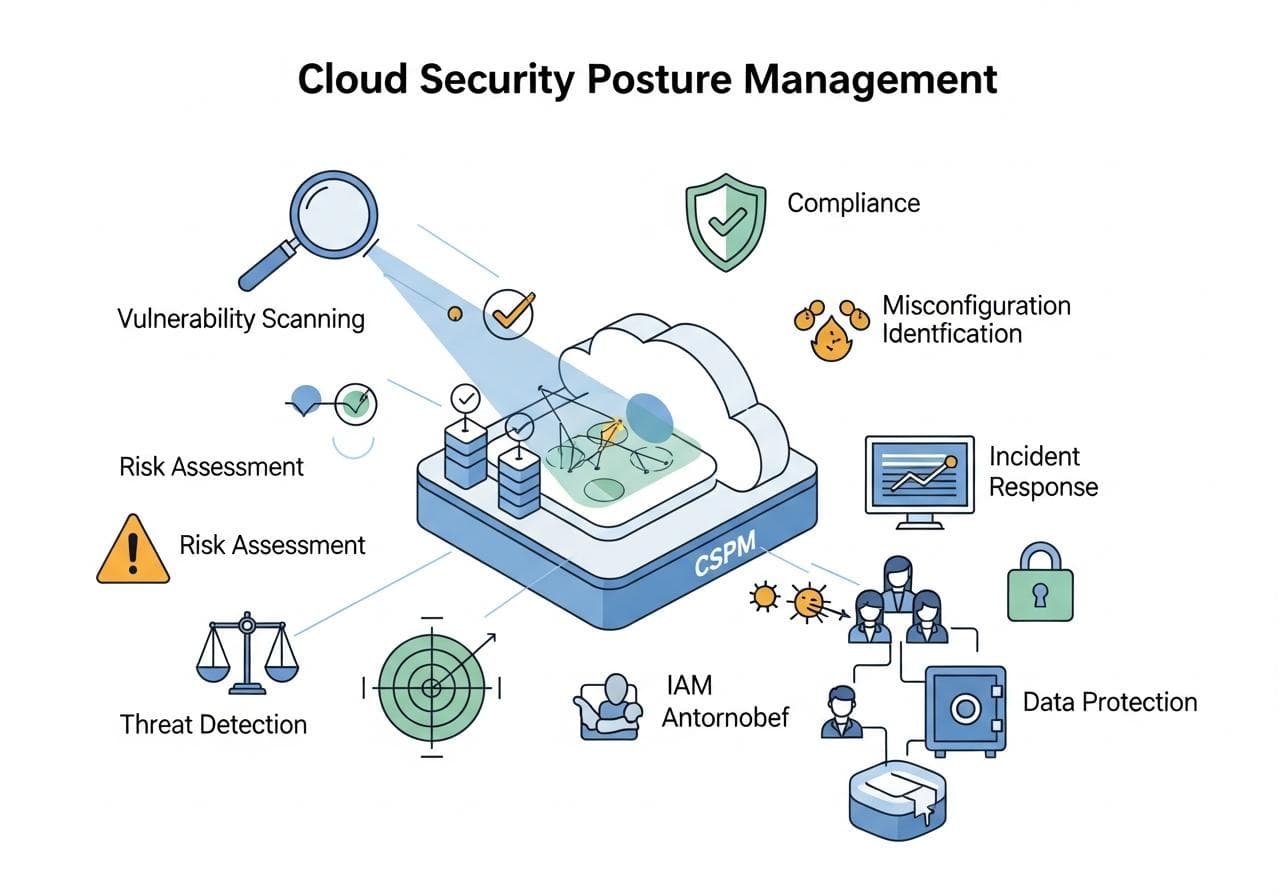
In today’s digital landscape, securing your cloud environment has become crucial, especially with the growing reliance on cloud services. Cloud Security Posture Management (CSPM) is a pivotal approach to maintaining a robust security posture in the cloud. Effective Data Protection hinges on implementing ideal CSPM strategies and best practices.
Understanding CSPM
CSPM stands for Cloud Security Posture Management. It involves continuously monitoring cloud infrastructure, identifying vulnerabilities, and ensuring compliance with security policies. This proactive measure helps in managing misconfigurations and mitigating risks associated with cloud services, ultimately enhancing your organization's security posture.
The Importance of Vulnerability Management
Vulnerability Management is a critical facet of CSPM. Identifying vulnerabilities before they are exploited is vital to protecting sensitive data. Regular assessments can highlight weaknesses in your cloud setup, allowing teams to address potential issues before they escalate into threats. Integrating automated vulnerability scanning tools can significantly aid in continuous monitoring and quick mitigation.
Compliance Matters
Being compliant with industry regulations is more than just a checkbox; it's essential for protecting customer data and maintaining trust. Understand the compliance requirements relevant to your organization, and leverage CSPM solutions to routinely check your cloud environments against these standards. Regular audits will not only reduce risks but also ensure that your data protection strategies are compliant with regulations such as GDPR, HIPAA, or PCI-DSS.
Addressing Misconfiguration
Misconfiguration is one of the leading causes of cloud breaches. With the elasticity of cloud environments, configurations can change rapidly, leading to gaps in security. CSPM tools can help in detecting these misconfigurations, providing real-time alerts to prevent data exposure. Establishing a configuration standard and continuously monitoring against it is key to ensuring that your configurations remain secure.
Conducting Risk Assessments
Regular risk assessments should be part of your CSPM strategy. Assessing risk involves identifying assets, potential threats, and the likelihood of incidents. This process helps prioritize vulnerabilities and focuses your remediation efforts on the most critical risks to cloud security. By incorporating regular risk assessments, organizations can maintain a resilient security posture and effectively protect sensitive data.
Enhancing Threat Detection
Threat detection must evolve alongside your cloud architecture. Utilize CSPM tools that incorporate machine learning and AI for enhanced visibility and alerts about potential threats. Automated incident detection can streamline your security operations, allowing for quicker response times, which is critical in today’s fast-paced environment.
Efficient Incident Response
No security strategy is complete without a solid Incident Response plan. CSPM should include protocols and tools for incident management that ensure quick action in case of a security event. Identify the roles and responsibilities of your incident response team and regularly conduct drills to refine the process. A structured incident response improves your organization's ability to minimize damage during a breach.
Implementing Identity and Access Management (IAM)
Identity and Access Management (IAM) is integral to data protection in cloud environments. With CASPM, ensure robust IAM practices by limiting user access based on what is necessary for their role. Integrating Multi-Factor Authentication (MFA) can also add a layer of protection. Effective IAM strategies reduce the likelihood of unauthorized access and are crucial for safeguarding sensitive data.
Data Protection as a Priority
Ultimately, the goal of CSPM should be to ensure effective Data Protection. This means not just focusing on technical controls but also fostering a culture of security within your organization. Regularly train staff on security best practices, invest in security solutions, and encourage a proactive attitude in recognizing and addressing security threats.
Conclusion
In summary, Cloud Security Posture Management is essential for any organization relying on cloud services. By adapting best practices in areas such as vulnerability management, compliance, misconfiguration detection, risk assessments, threat detection, incident response, and IAM, you can significantly enhance your data protection efforts. For those seeking a starting point, consider exploring options like AWS’s Cloud Security Posture Management solution, which can help streamline your approach.
With the right strategies in place, your organization can effectively safeguard its data, maintain compliance, and stay one step ahead of potential security threats.
Posts Relacionados

Anomaly Detection In Network Traffic Using Machine Learning
Machine learning identifies unusual network traffic, improving network path monitoring and security through real-time analysis.
Application Performance Monitoring
Network diagnostics provide insights. Performance bottlenecks identified, resolved, enhancing network efficiency and user experience.
Assessing Thirdparty Risk
Effective management of third-party risk protects business operations through diligent evaluation and proactive mitigation strategies.